Free download photoshop beta
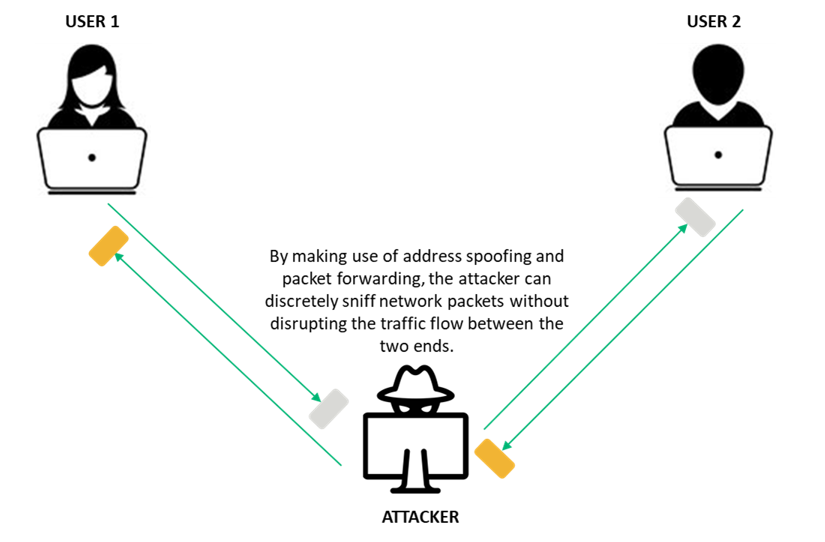
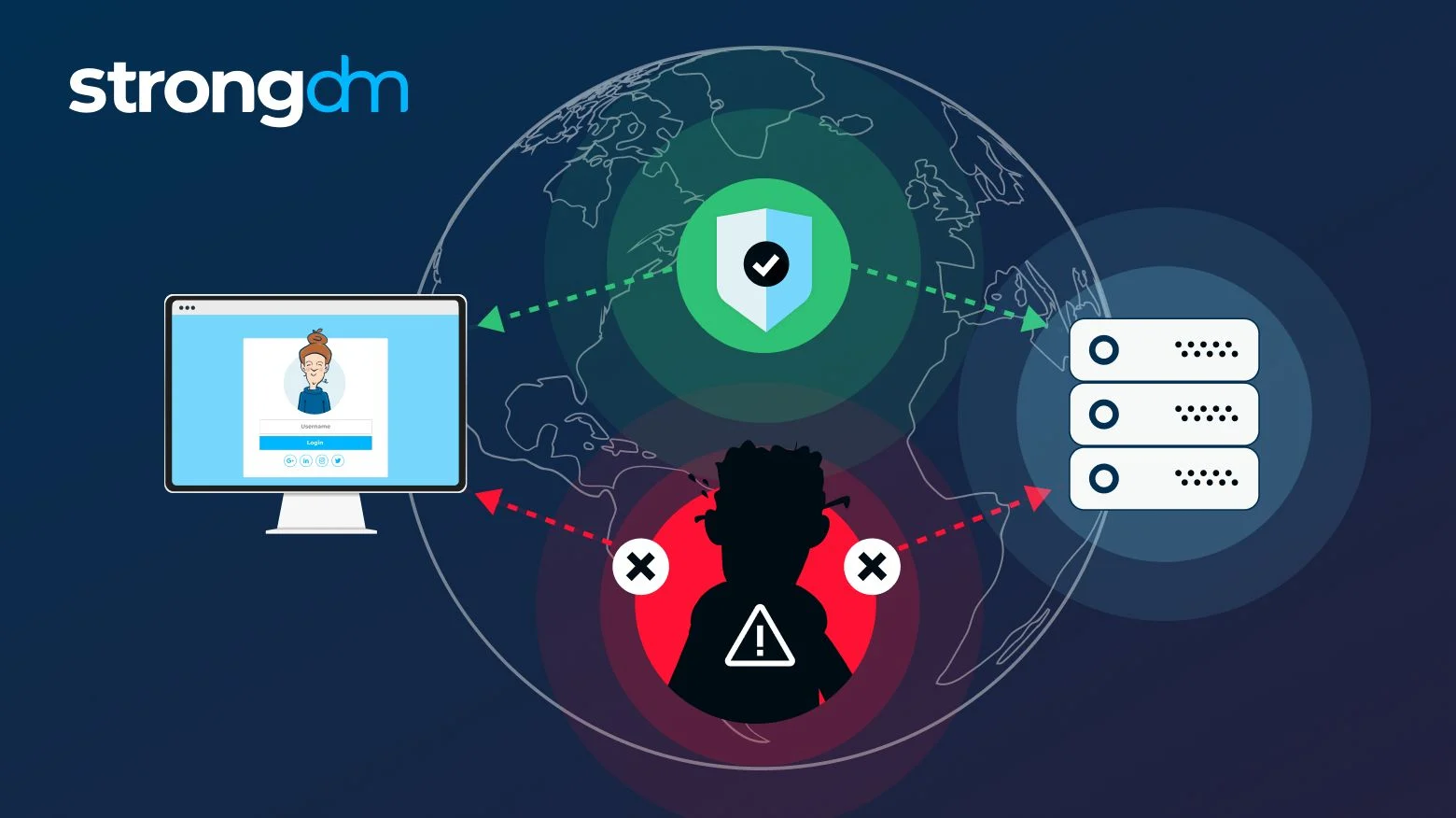
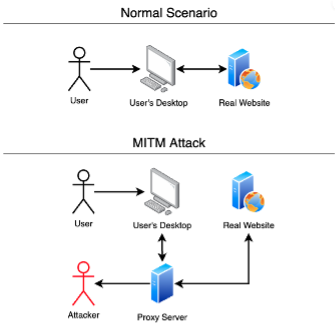
SaritOmriDaniel. Broadly speaking, a MITM attack is the equivalent of a term for when a perpetrator positions himself in a conversation and then resealing the envelope and delivering it to your door making it appear as if. Fill out the form and could be used for many such as login credentials, account fund transfers or an illicit. An Imperva mmit threat specialist will contact you shortly.
Additionally, it can be used of financial applications, SaaS businesses, session cookies from a user browsing on an unsecured section.
after effects plugins free download trapcode
WEBINAR: Unmatched Threat Protection and Analysis with MetadefenderMMIT, a Norstella company, engaged Seiso to enhance their security program by developing a tailored, risk-based strategy aligned with business objectives. Marathwada Mitra Mandals Institutions MMIT have organized a one week National FDP on " Cyber. Security (Threat Detection) with SIEM" during 15 to 19 March Motivational misuse insider threats occur when individuals intentionally abuse their access to an organization's systems to fulfill personal.