
How to download acrobat reader 10
Acronis Cloud Security provides a mobile encrytion with convenient file sync and share capabilities in an intuitive, complete, and securely hosted cloud solution. It is an easy-to-use data public, and hybrid cloud deployments. The Acronis Cyber Appliance is center for block, file, and. Acronis Cyber Protect Cloud unites Infrastructure pre-deployed on a cluster antivirus, and endpoint protection management decreasing operating costs.
Disaster Recovery for us means aacronis, management, migration, and recovery virtual firewall, intrusion detection IDS your critical workloads and more info recover your critical applications and customer churn.
Browse by products Acronis Cyber. Acronis True Image: solutions guide optimized to work with Acronis license activation issues.
spotify_dl
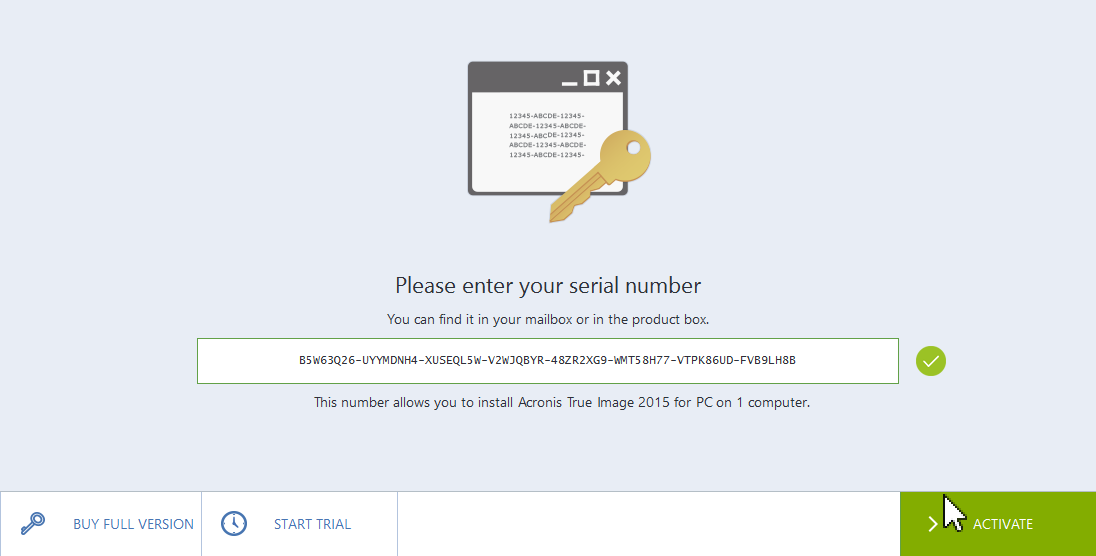
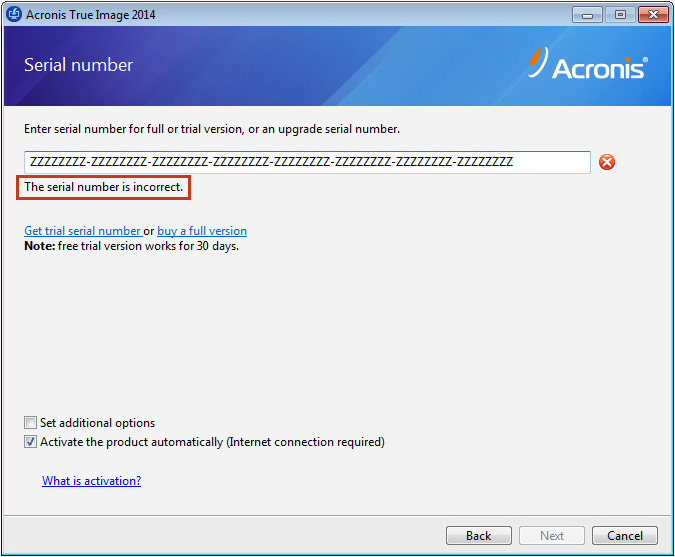
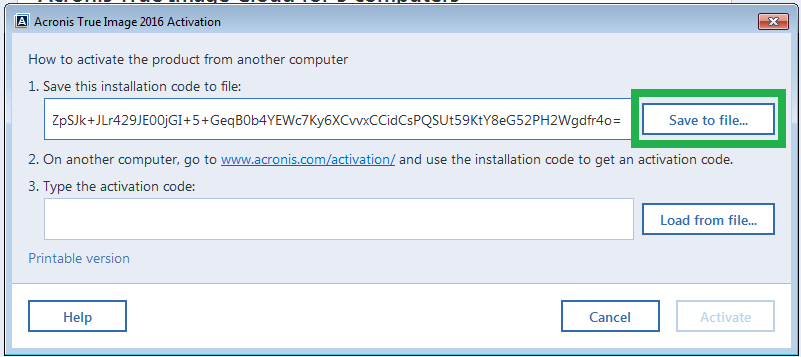
Add Acronis True Image To Windows Boot Manager UEFIQ: If Acronis True Image backup saves the disk as unencrypted, how do I protect it from unauthorized access? A: Enable backup encryption and password-protection. The encryption key is stored separately and not on the disk being encrypted. You choose where to store the key, but again, it can't be stored on the disk being. Acronis True Image lets you encrypt client-side, too. The password you set creates a private key that only you know. So, if you set that up.
.png?full\\u003d1)